Network Based Firewall Examples

Most operating systems provide a firewall to protect the host computer often called a host firewall.
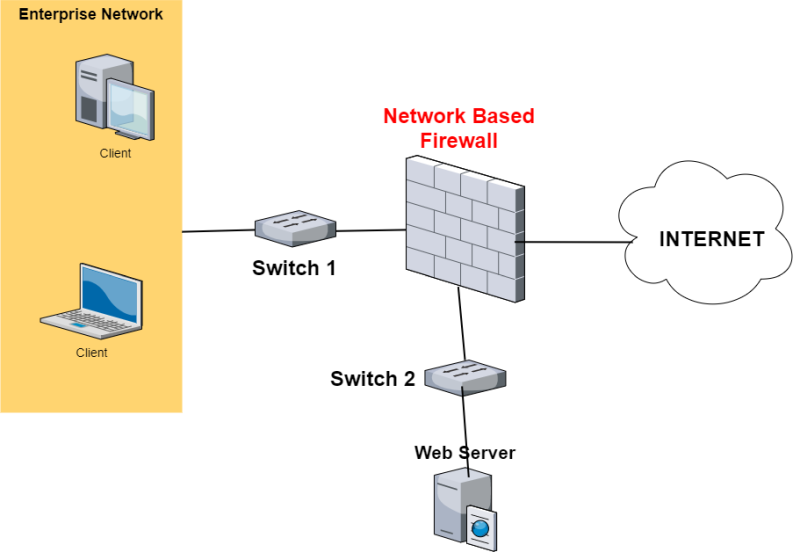
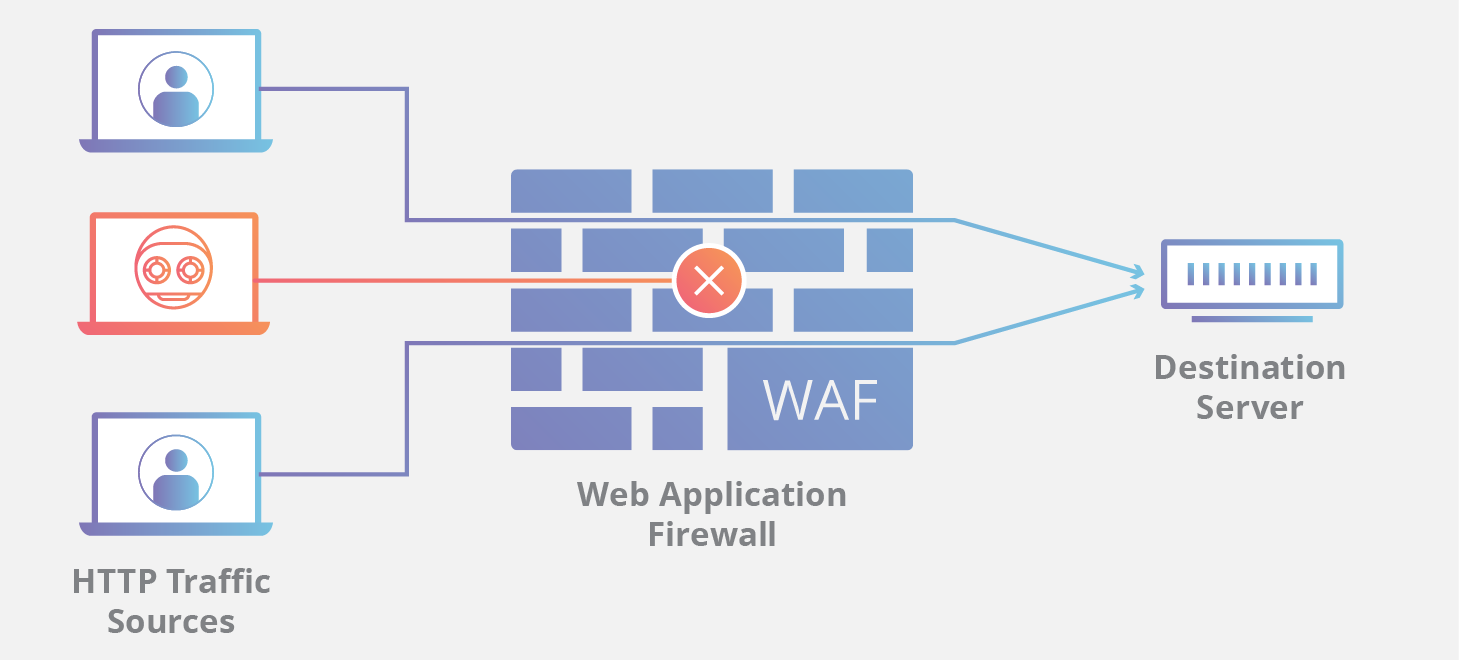
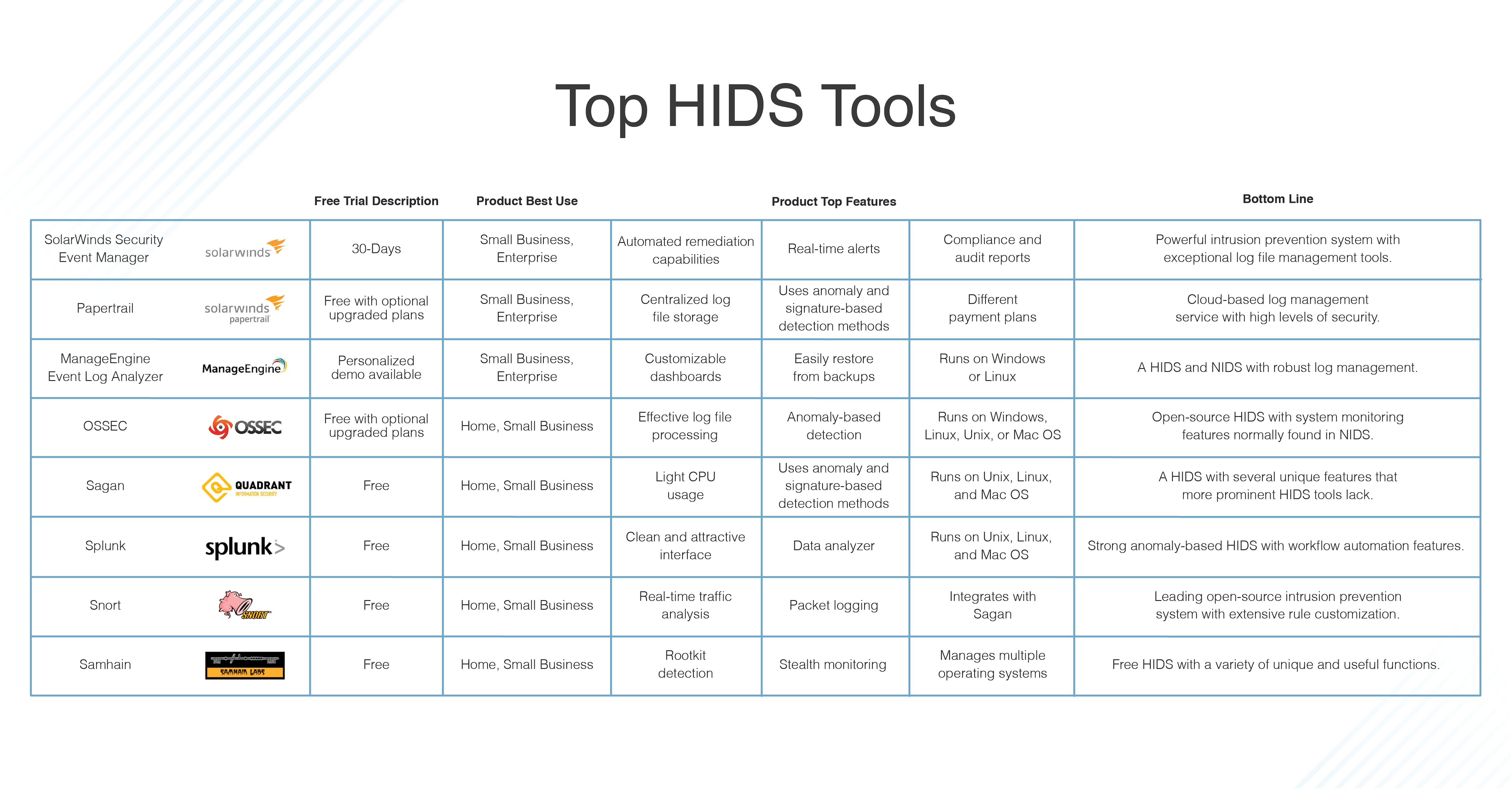
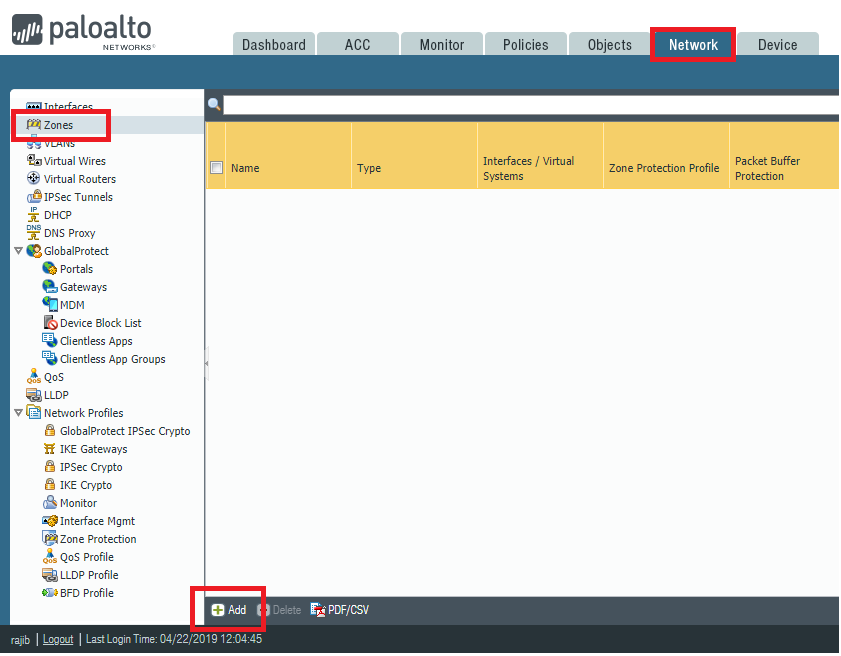
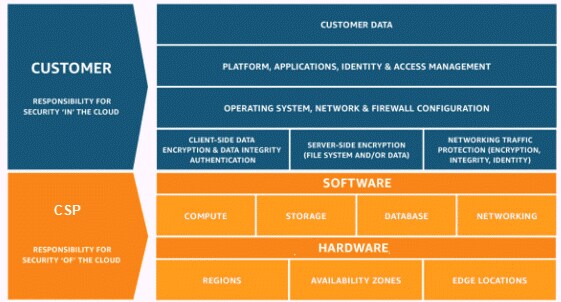
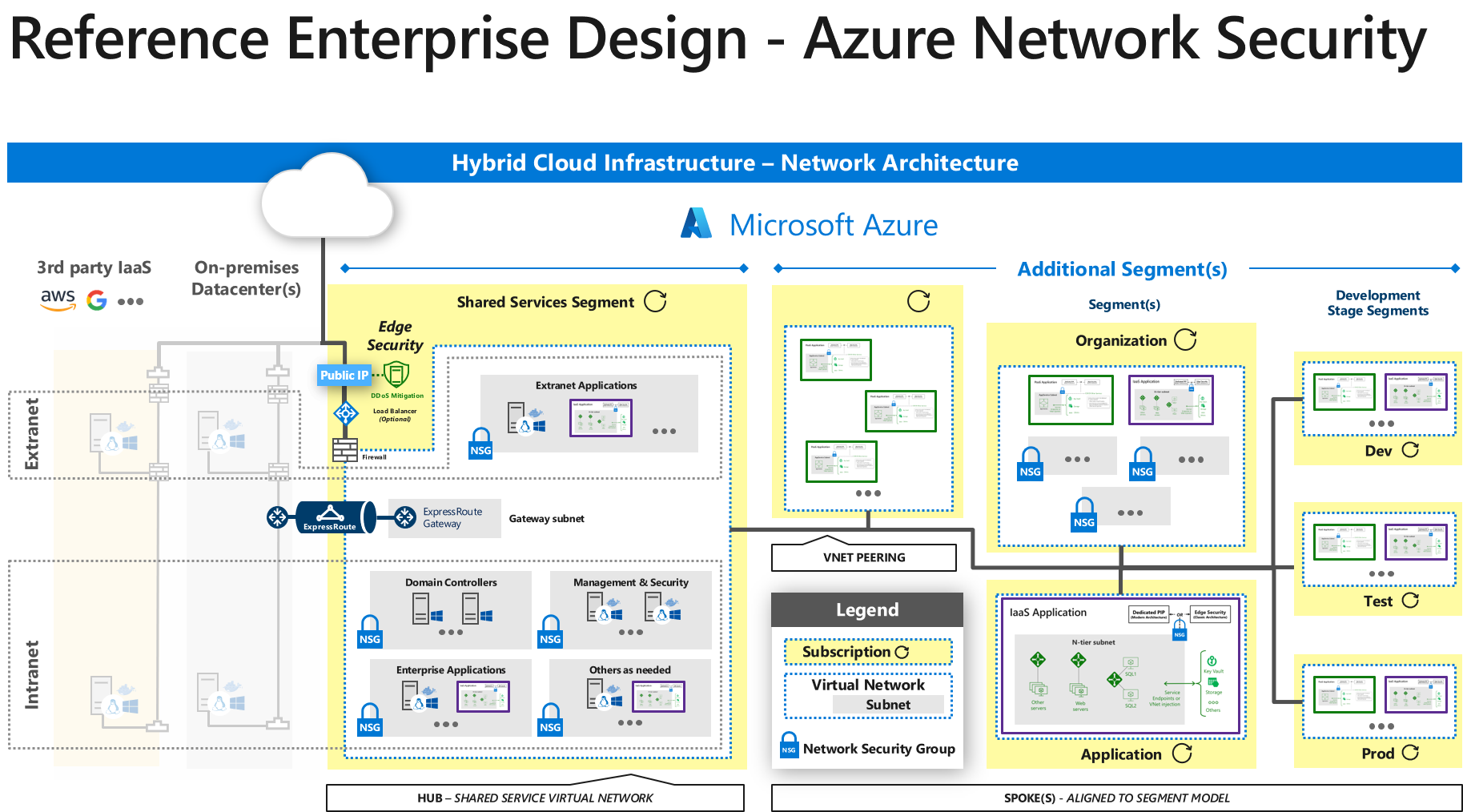
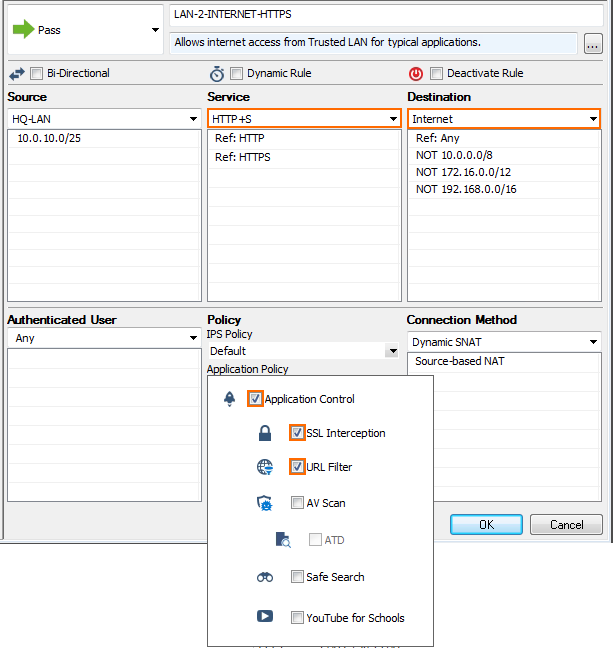
Network based firewall examples. These types of firewalls are a granular way to protect the individual hosts from viruses and malware and to control the spread of these harmful infections throughout the network. A firewall that filters ip traffic between apair of bridged interfaces. This allows it to identify unwanted applications or services using a non standard port or detect if an allowed protocol is being abused. A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
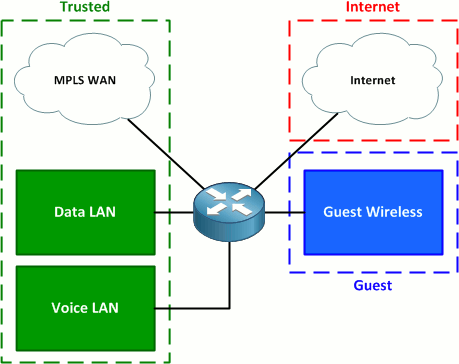
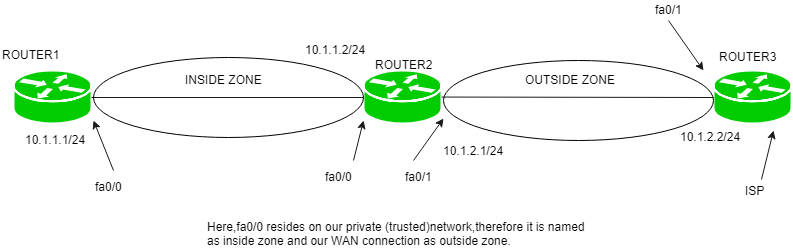
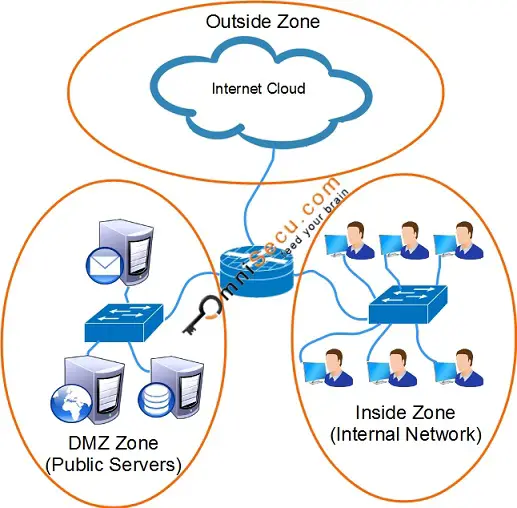
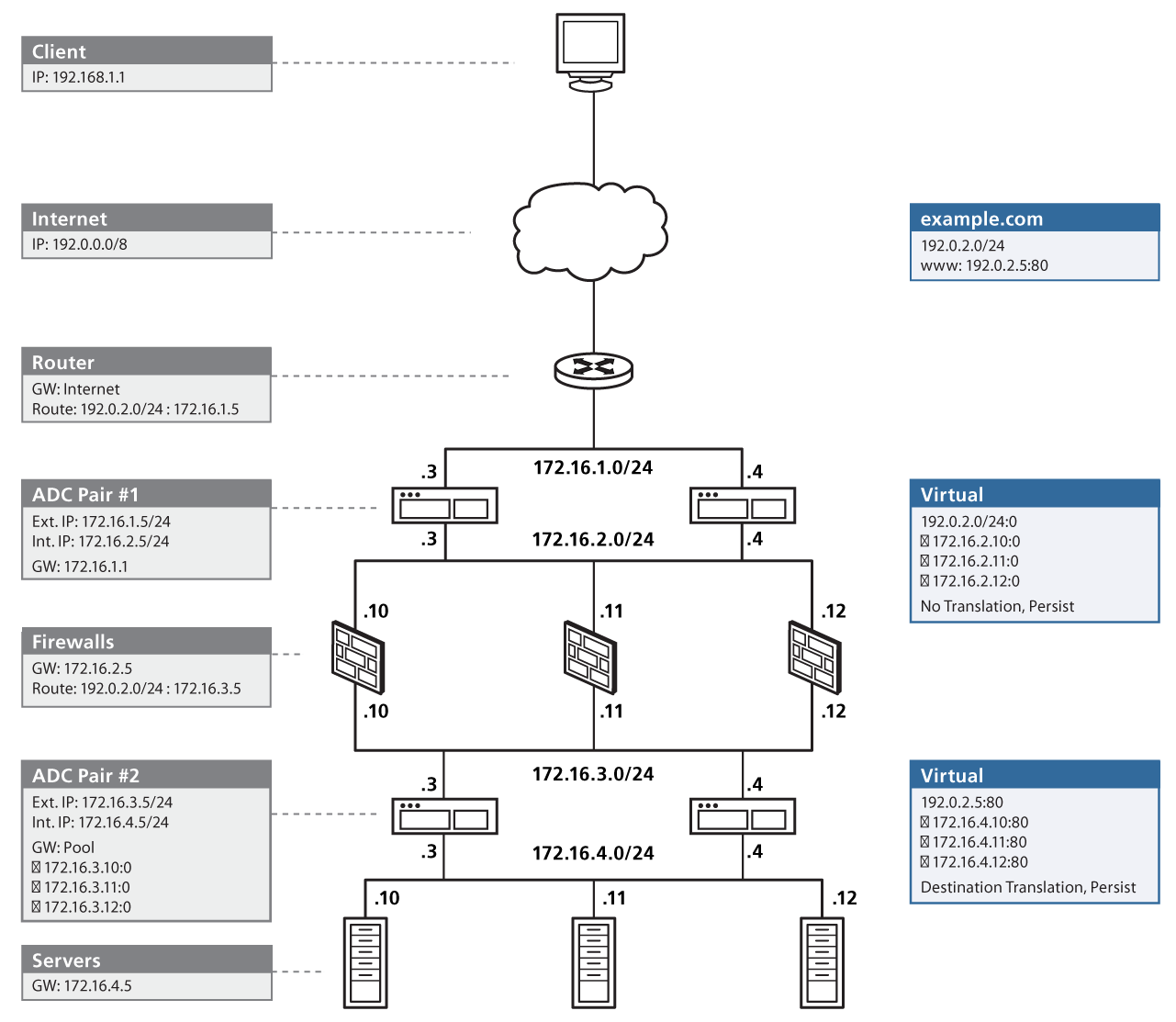
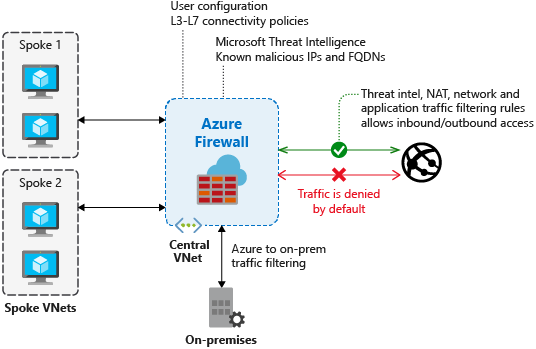
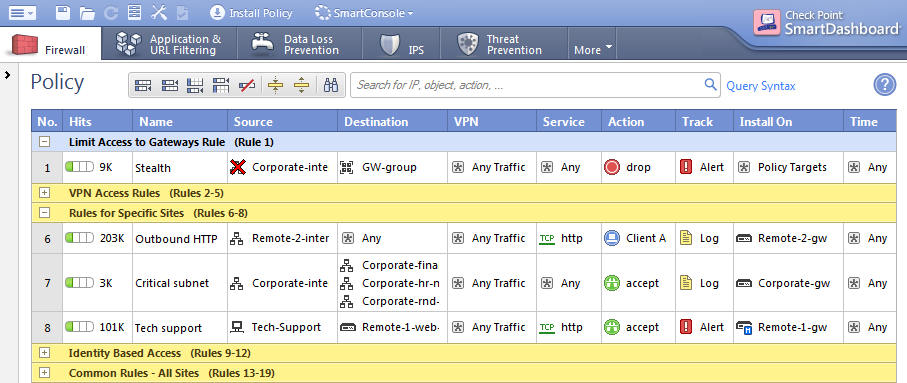
What is a network based firewall as the name implies this type of firewall is mainly used to protect whole computer networks from attacks and also for controlling network traffic so that only allowed packets are able to reach your servers and it assets. The picture above shows several cisco asa network based firewalls. The network based firewall is usually a dedicated system with additional software installed to monitor filter and log traffic. For example an application inspection firewall combines a stateful firewall with an application gateway firewall.
Firewall appliances may also offer non firewall functionality such as dhcp or vpn services. Firewalls have been a first line of defense in network security for over 25 years. This can be a daemon or service as a part of the operating system or an agent application for protection. This is a dedicated server with proprietary firewall software installed.
Host based firewalls are deployed directly on the host itself to control network traffic or other computing resources. A network based application firewall operates at the application layer of a protocol stack and can understand certain applications and protocols such as file transfer protocol ftp domain name system dns or hypertext transfer protocol http. For example iptables is the firewall application provided as a part of the linux operating system. Related firewall vs ips vs ids it s notable to share that network firewall does not know about the applications and vulnerabilities on a machine or vm only the os will know that and host based firewall will be the best bet to provide security to the os eend system the major benefit of using host based firewall is that since the protection system is installed in the host itself it is.
Several major firewall companies offer a software version of their network firewall. For example a popular network based firewall used in many larger environments is sidewinder.